#SQL SERVER Online Test questions for experienced
Explore tagged Tumblr posts
Text
Boost Your Web Development Skills: Akhilagna’s Key Learning Resources
In the ever-evolving world of web development, staying ahead requires continuous learning and the ability to adapt to new tools, technologies, and methodologies. Whether you're an aspiring developer or a seasoned professional, accessing quality resources can make all the difference in boosting your skills. At Akhilagna IT, we understand the significance of empowering developers with the right learning tools and resources. This article highlights some of the key learning resources we offer to help you thrive in your web development journey.
Comprehensive Online Tutorials
Akhilagna’s curated online tutorials are designed to cater to developers at various skill levels. From foundational concepts like HTML, CSS, and JavaScript to advanced topics such as frameworks, libraries, and backend development, our tutorials provide step-by-step guidance. Each tutorial is enriched with real-world examples, ensuring that learners can directly apply what they learn in practical scenarios.
For beginners, we cover essentials like:
Structuring web pages with HTML
Styling elements using CSS
Interactive user interfaces with JavaScript
For advanced developers, topics include:
Working with modern frameworks like React, Angular, and Vue.js
Server-side programming with Node.js and Django
Managing databases using MongoDB and SQL
Interactive Coding Challenges
Learning by doing is one of the most effective ways to develop technical skills. Our platform offers interactive coding challenges that allow you to test your knowledge and sharpen your problem-solving abilities. These challenges are tailored to simulate real-world development tasks, such as debugging code, optimizing performance, and creating scalable web solutions.
Expert-Led Webinars and Workshops
At Akhilagna, we believe in the power of live learning experiences. Our expert-led webinars and workshops provide opportunities to learn from industry professionals who share their insights, experiences, and best practices. Topics range from the basics of responsive design to mastering cloud integration and DevOps practices.
Workshops often include hands-on projects, allowing participants to apply their skills under the guidance of experienced mentors. These sessions also provide a platform to ask questions, seek feedback, and interact with peers in the development community.
Resourceful Blogs and Articles
Our blog section is a treasure trove of articles covering a wide array of web development topics. Whether you're looking to understand the latest trends, explore in-depth tutorials, or discover tips for career growth, our blogs cater to diverse interests and needs. Written by experts, these articles provide actionable insights that can help you stay updated in this fast-paced field.
Project-Based Learning Opportunities
Akhilagna emphasizes the importance of project-based learning to bridge the gap between theory and practice. By working on real-world projects, developers can gain hands-on experience, build their portfolios, and develop a deeper understanding of web development concepts. These projects span areas like e-commerce site creation, API development, and single-page application (SPA) design.
Community Support and Collaboration
Becoming part of a supportive community can significantly enhance your learning experience. Akhilagna’s developer community offers a collaborative space where members can share ideas, seek advice, and discuss the latest trends in web development. Through forums, group projects, and networking events, developers can connect with like-minded professionals and expand their horizons.
Conclusion
In the dynamic landscape of web development, continuous learning is not just an option but a necessity. Akhilagna IT is dedicated to equipping developers with the knowledge, skills, and tools they need to excel. By leveraging our tutorials, coding challenges, webinars, and other resources, you can stay ahead in your career and tackle complex development challenges with confidence. Explore Akhilagnait Services offerings today and take the next step in your web development journey!
0 notes
Text
Hello Coding - Anyone Can Learn to Code! 550+ Hours of Content!

"Hello Coding: Anyone Can Learn to Code!" is an expansive online course designed to introduce and deepen understanding of computer programming for individuals at all skill levels. With over 550 hours of meticulously curated content, the course aims to transform beginners into proficient coders and to help experienced programmers refine and expand their skills.
Course Structure and Content
The course is structured to cover a broad range of programming topics and languages. Starting from the basics, it gradually progresses to more complex concepts, ensuring that learners build a solid foundation before tackling advanced subjects. Key areas covered include web development, mobile app development, data science, and game development, among others.
Introduction to Programming: The course begins with an introduction to programming fundamentals. It covers the basic principles of coding, such as variables, control structures, functions, and data types. This section is designed to be accessible to complete novices, with no prior experience required.
Web Development: This segment delves into HTML, CSS, and JavaScript, teaching learners how to create and style web pages. It also covers popular frameworks and libraries like React, Angular, and Vue.js, which are essential for modern front-end development. On the back-end side, it explores server-side languages like Node.js, Python, and PHP, along with databases such as SQL and MongoDB.
Mobile App Development: Learners are introduced to mobile app development for both Android and iOS platforms. The course covers native app development using Swift for iOS and Kotlin for Android. It also explores cross-platform development frameworks like Flutter and React Native, which allow developers to create apps that work on multiple operating systems from a single codebase.
Data Science and Machine Learning: For those interested in data science, the course offers comprehensive modules on Python, R, and various data analysis libraries and tools. It covers data visualization, statistical analysis, and machine learning algorithms. This section is ideal for learners who wish to pursue careers in data science or integrate data-driven decision-making into their existing skill set. You can also try this HELLO CODING
Game Development: The course includes modules on game development using popular engines like Unity and Unreal Engine. It covers the basics of game design, programming, and the creation of both 2D and 3D games. This segment is particularly appealing to creative individuals who want to bring their game ideas to life.
Learning Approach
"Hello Coding" adopts a project-based learning approach. This means that instead of just theoretical learning, students engage in hands-on projects that allow them to apply what they have learned. These projects range from simple exercises to complex applications, ensuring that learners can see the real-world applications of their coding skills.
The course also emphasizes interactive learning. Through coding challenges, quizzes, and peer interactions, learners are encouraged to test their knowledge and learn from others. This interactive environment helps to reinforce learning and fosters a sense of community among participants.
Support and Resources
Learners have access to a wealth of resources to support their learning journey. These include detailed video tutorials, comprehensive reading materials, and practical coding exercises. Additionally, the course provides access to mentors and instructors who can offer guidance and answer questions.
Career Preparation
One of the standout features of "Hello Coding" is its focus on career preparation. The course includes modules on resume building, portfolio development, and interview preparation. This ensures that learners are not only equipped with technical skills but are also prepared to enter the job market with confidence.
Conclusion you can also try this HELLO CODING
"Hello Coding: Anyone Can Learn to Code!" is an all-encompassing course that caters to a wide audience, from complete beginners to experienced developers. Its extensive content, project-based approach, and focus on career preparation make it an invaluable resource for anyone looking to start or advance their coding journey. With over 550 hours of content, learners have the opportunity to explore various fields within programming, find their niche, and build a successful career in the tech industry.
DISCLAIMER
There is an affiliate link for a best product in this article which may make some profit for me
0 notes
Text
Mastering the Full Stack: Essential Interview Topics for Developers
Absolutely! I’m thrilled to explore the realm of full-stack development with you. My proficiency in this field has expanded significantly over time. Selenium has become widely recognized and extensively employed, cutting across various industries. Advance your career in Full-Stack Developer at a Top Institution in Chennai, like ACTE Technologies.

Preparing for a full-stack developer interview requires a thorough grasp of both front-end and back-end technologies.
Focus On The Following Key Topics:
1. HTML, CSS, and JavaScript:
Understand fundamental concepts and best practices for creating web pages and dynamic content.
2. Front-End Frameworks:
Explore React, Angular, or Vue.js, including component-based architecture and state management.
3. Responsive Design:
Implement techniques ensuring seamless application functionality across various devices and screen sizes.
4. Server-Side Languages:
Demonstrate proficiency in at least one language, such as JavaScript (Node.js), Python, Ruby, Java, or PHP.
5. Server Frameworks:
Utilize Express.js (Node.js), Django (Python), Ruby on Rails (Ruby), or others, with a focus on routing, middleware, and handling HTTP requests.
6. Database Management:
Showcase knowledge of both SQL and NoSQL databases, including CRUD operations and database design.
7. RESTful APIs:
Exhibit expertise in designing and consuming APIs for effective front-end to back-end communication.
8. Version Control:
Display proficiency in Git, encompassing understanding of branching, merging, and conflict resolution.
9. DevOps and Deployment:
Illustrate familiarity with deployment processes, tools, and cloud services like AWS, Azure, or Google Cloud.
10. Security Best Practices:
Demonstrate understanding of data protection, encryption, and user authentication.
11. Testing:
Showcase expertise in testing methodologies and frameworks (e.g., Jest) for ensuring code reliability.
12. Command Line/CLI:
Exhibit proficiency in using the command line for various tasks.
13. Agile/Scrum Methodologies:
Showcase understanding of Agile development practices for effective teamwork.
14. Soft Skills:
Emphasize communication, problem-solving, and teamwork skills.
15. Algorithm and Data Structures:
Brush up on fundamental algorithms and data structures.
16. System Design:
Demonstrate a high-level understanding of designing scalable and efficient systems.

Remember to tailor your preparation based on the specific job description and requirements of the position. Additionally, be ready to highlight relevant past projects and experiences in the full-stack development domain during the interview.
If you’re keen on exploring Full-stack Developer course in Chennai, I highly recommend considering Top Institutions like ACTE Technologies. They provide certification programs and job placement opportunities, guided by experienced instructors to enhance your learning journey. These resources are available both online and in-person. Enrolling in a course step by step could prove to be a valuable decision if it aligns with your interests.
I trust this addresses your query adequately. If you have more questions or need further clarification, please feel free to ask in the comments section.
If you’ve found this information valuable, I invite you to follow me on this platform and give it an upvote to encourage more discussions and insights about Full-stack Development. Your time and engagement are greatly appreciated, and I wish you a wonderful day ahead.
0 notes
Link
#SQL SERVER Online Test#SQL SERVER Online Test Question#SQL SERVER questions#SQL SERVER#SQL SERVER Questions For Online Test#Best SQL SERVER Online Test Questions#SQL SERVER Online Test Questions For Freshers#SQL SERVER Online Test questions for experienced#most common SQL SERVER Online Test questions#Top 20 SQL SERVER Online Test questions#Top 50 SQL SERVER Online Test questions#sql online coding test#sql interview test#sql test questions and answers#sql practice questions
0 notes
Text
Data And Information Security For Today's Business
Data and data security has grown into probably one of the most important problems facing the current companies yet it is overlooked. Were you aware according to your Deloitte Touche Survey a lot more than 50 percent of businesses admitted to using a data-loss between June 2005 and June 2006? Roughly 33 percent of them resulted in financial loss. A poll by Zoomerang revealed that 34 percent of organizations usually do not own a security policy 0that prohibits downloading non-business software on company-owned computers. In 2005 55 percent of online users reported being infected with spy ware based to some Bigfoot Interactive poll.

For smaller organizations, every dollar spent about it will need to have a proven firm value. For security services and products which is sometimes a challenging endeavor. If you don't have undergone an attack in your own webserver, a SQL injection attack in your own e commerce site, or experienced a virus epidemic in your own system many managers and decisionmakers balk at the notion of spending money on the package of network security solutions.
Just because it's problematic for a house owner that goes into Florida to find it could be worth it to pay $5-10k on storm shutters, it's challenging for managers to comprehend putting a considerable part of their own IT budget to security solutions. But if exact same homeowner has lived during two or three storm seasons or starts speaking about their neighbors concerning what the 2005 season has been similar to it generally does not require them before not only are they really willing to devote the amount of money, however they can not wait to accomplish it. The short coming of the analogy is the fact that the possible loss to get a organization might be worse compared to a homeowner along with too often there's not insurance to pay for lost revenue. To make it more challenging you can even be held responsible for not taking appropriate action to safeguard your visitors confidential information.
Some relevant questions to get a manager or small business owner to buy them believing in proper direction is: What will happen if our servers are stolen? What could happen to this organization if your fire burnt down work and every bit of technology has been lost? What is the results in case our competitors could acquire access to trade secrets? What could be the legal consequences? Can it be revived? Howmuch downtime on the network can we live? How could this affect the general public image of the company?
The replies to those questions are frequently hard to come to grips with. Too frequently managers ignore them and also do not provide them the care they have. In place, they have been playing with the likelihood that will not happen in their mind and so they don't get ready what is an incredibly real and imminent threat. Data and data security isn't at all something they know or have expertise this that they discount it and treat it not really a true threat. Therefore whatever reasons , their confidential and critical small business data remains insecure and so they don't have any systems in place to examine or track activity in their own network apparatus or prevent a potential hook from occurring.
It's also extremely crucial to not forget that the high proportion of strikes come out of the inside, not the outside your system. Disgruntled employees will pose a high security hazard. Additionally, your organization will not need to need to become described as a"target". Many strikes are generated by arbitrary scripts which hunt for any receptive target. The question will you're prepared to this if that effort is manufactured or would an attacker be too prepared to benefit from one's unprotected network?
Therefore what's the ideal outlook or approach? The ideal view is the fact that the potential for an attack or attempted usage of unauthorized data rather than merely going but merely an issue of time. Such as insurance, an appraisal ought to be carried out regularly to be certain that the perfect sort of"policy" is inplace. The executive control should play a major part in deciding what advice has become easily the absolute most private such that it may precisely shielded.
Therefore what's a company proprietor? Just take enough time for an extensive strategy to the security of your advice. Put a small business security policy set up and stay with it. This might consist of consulting one or more security experts that focus on this kind of work. Perhaps this is something as straightforward as ensuring that your Broadcom españa internal IT team has been taken the necessary measures, however to begin dealing together with them from the direction degree. Section of one's policy ought to be described as a scheduled testing and advancement into the security measures in place. Network and data security isn't really a static solution which you are able to employ once and leave . It's some thing which has to be tracked, analyzed, and improved on an everyday basis.
The fantastic thing is a secure setting for your own computer data can be gained. Perhaps it doesn't appear easily and there'll soon be an amount attached to this, however, the fee mounted on staying un-secured is higher.
1 note
·
View note
Text
Microsoft SQL Server 70-463
Published: June 11, 2012 Languages: English, Chinese (Simplified), French, German, Japanese, Portuguese (Brazil) Audiences:IT professionals Technology: Microsoft SQL Server 2012/2014 Credit toward certification: MCSA, MCSE Implementing a Data Warehouse with Microsoft SQL Server 2012/2014 $165.00 USD Microsoft 70-463 exam might be available in your country for online proctored delivery. Pricing won't reflect any promotional offers or reduced pricing for Microsoft Imagine Academy program members, Microsoft Certified Trainers, and Microsoft Partner Network program members. Cost is subject to change without warning. Pricing won't include applicable taxes. Record exact pricing with the exam provider before registering to look at a test. Effective May 1, 2017, the present cancellation policy will likely be replaced as a whole together with the following policy: Cancelling or rescheduling your exam within 5 days of one's registered exam time is be subject to a fee. Failing to make an appearance for the exam appointment or otherwise not rescheduling or cancelling your appointment at the very least A day just before your scheduled appointment forfeits your entire exam fee.

Skills measured 70-463 exam measures what you can do to complete the technical tasks further down. The percentages indicate the relative weight of each and every major topic area for the exam. The higher the percentage, the more questions you may well see on that content area on the exam. View video lessons concerning the selection of question types on Microsoft exams. Are you experiencing feedback in regards to the relevance with the skills measured about this exam? Please send Microsoft your comments. All feedback is going to be reviewed and incorporated as appropriate while still maintaining the validity and robustness of the certification process. Be aware that Microsoft will not likely respond right to your feedback. We appreciate your input in ensuring the caliber of the Microsoft 70-463 Certification program. When you've got concerns about specific questions about 70-463 exam, please submit a test challenge. If you have other questions or feedback about Microsoft 70-463 Certification exams or in regards to the certification program, registration, or promotions, please contact your Regional Service Center. Since February 18, 2016, 70-463 exam includes content covering both SQL Server 2012 and 2014. Please be aware that this exam does not include questions about features or capabilities which might be present only inside the SQL Server 2012 product. For more info, please download and review this document. Design and implement a knowledge warehouse (10-15%) Extract and transform data (20-25%) Load data (25-30%) Configure and deploy SSIS solutions (20-25%) Build data quality solutions (15-20%) Preparation options Instructor-led training Exam prep videos Self-paced training Practice test From town Books To learn more about 70-463 Certification go to the best web page.
1 note
·
View note
Text
Cyber security courses in Malaysia
In Malaysia, Cyber security courses are in high demand. Professionals are continuously seeking opportunities to enhance their skill sets. However, the question remains whether Malaysian universities offer enough cyber security courses?
The Malaysian government has made the cyber security courses an essential part of its National Key Economic Area (NKEA) to ensure that its cyber security is not compromised shortly. The country's top universities are offering their degrees in cyber security and related fields with many students taking up these courses. Cyber security is a field that has been in existence for many years now. However, the need to provide quality cyber security professionals to the market demands that universities stay ahead of time and design suitable courses.
In Malaysia, there are close to thirty higher educational institutions offering cyber security courses at undergraduate and postgraduate levels. This includes highly recognized universities such as the University of Malaya, the National University of Malaysia, and Universiti Teknologi Malaysia. Several courses can be chosen from in cyber security and students who want to study information and network security could opt for a Bachelor's degree in Information Systems Security.
But, When it comes to short-term courses in Cyber Security there are very few options. I3Matrix is one such organization that provides comprehensive Cyber security courses in Malaysia. Courses are well designed and structured and students can choose to learn and acquire skills in either Ethical Hacking, Computer Forensics, or Network Penetration Testing.
I3Matrix is Malaysia's leading Cyber Security training center and we offer courses that are industry recognized and the course contents are designed by highly experienced trainers from industry-leading organizations such as Microsoft, Cisco, VMware, etc…
- Ethical Hacking Online Training in Malaysia
This Cyber Security training module focuses on ethical hacking techniques that can be used by students. The students will learn about Penetration Testing and Distributed Network Scanning using various tools such as Metasploit, Backtrack Linux, etc,… Since the module is designed with hands-on training in mind, students can expect to work on projects that help them further enhance their skills.
Ethical Hacking Training Module Covers:
Ethical Hacking Basics
Types of Attack Methods
Reconnaissance Attacks
Social Engineering Attacks
Hacking Wireless Networks
SQL Injection attacks & Defenses
Malware Reverse Engineering Online Training in Malaysia - Network Penetration Testing Online Training in Malaysia - Cryptography Online Training in Malaysia - Cyber Security Investigations Online Training in Malaysia
This Cyber Security training module covers all aspects of security operations including vulnerability management, incident response using digital forensics tools. The students will learn how to manage various types of vulnerabilities found on web servers, IDS/IPS systems, etc…The module also teaches how intrusion detection systems work and how to create effective policies for security.
- WLAN Pen Testing Online Training in Malaysia
- WiMAX Security Penetrating Online Training in Malaysia
- Mobile Phone Hacking & Security Online Training in Malaysia - SSL/TLS (HTTPS) Online Training in Malaysia For any inquiries regarding Cyber Security Courses in Malaysia, please contact us at 03-7967 1855 or you can email us at [email protected].
0 notes
Text
Navigating the Full Stack: Essential Skills Every Developer Should Possess
Certainly! I’m excited to embark on the journey of full-stack development with you. My proficiency in this domain has expanded significantly, and Selenium has gained widespread acclaim, finding extensive use across a variety of industries. Advance your career in Full-Stack Developer at a Top Institution in Chennai, like ACTE Technologies.

A comprehensive skill set is essential for a full-stack developer, encompassing both front-end and back-end technologies.
Here’s A Breakdown Of Key Areas:
1. Front-End Development:
Master core web technologies (HTML, CSS, and JavaScript) for building user interfaces.
Learn popular frameworks (e.g., React, Angular, or Vue.js) for efficient UI development.
Ensure responsive design for seamless functionality across various devices and screen sizes.
2. Back-End Development:
Develop proficiency in a server-side language (e.g., Node.js, Python, Ruby, Java, or PHP).
Gain familiarity with frameworks such as Express.js (for Node.js), Django (for Python), or Ruby on Rails.
Understand both SQL and NoSQL databases and excel in data storage and retrieval.
Design and consume RESTful APIs for effective communication between front-end and back-end.
3. Version Control/Git:
Master version control systems like Git for efficient collaboration and code management.
4. DevOps and Deployment:
Understand deployment processes and tools.
Familiarity with cloud services like AWS, Azure, or Google Cloud.
5. Basic Design Skills:
Acquire a foundational understanding of design principles to enhance the creation of user-friendly interfaces.
6. Security:
Apply knowledge of security best practices, including data protection and user authentication.
7. Testing:
Learn testing frameworks (e.g., Jest) to ensure code reliability.
8. Command Line/CLI:
Demonstrate proficiency in using the command line for tasks like file manipulation, server management, and version control.
9. Agile/Scrum Methodologies:
Grasp Agile development practices for effective teamwork and project management.
10. Soft Skills:
Cultivate effective communication, problem-solving, and teamwork skills crucial for collaboration in development teams.

Continuously staying abreast of industry trends and emerging technologies is imperative for a full-stack developer to adapt to evolving demands.
If you’re keen on exploring Full-stack Developer course in Chennai, I highly recommend considering Top Institutions like ACTE Technologies. They provide certification programs and job placement opportunities, guided by experienced instructors to enhance your learning journey. These resources are available both online and in-person. Enrolling in a course step by step could prove to be a valuable decision if it aligns with your interests.
I trust this addresses your query adequately. If you have more questions or need further clarification, please feel free to ask in the comments section.
If you’ve found this information valuable, I invite you to follow me on this platform and give it an upvote to encourage more discussions and insights about Full-stack Development. Your time and engagement are greatly appreciated, and I wish you a wonderful day ahead.
0 notes
Text
10 top API security testing tools

Application programming interfaces (APIs) are a critical part of most modern programs and applications. In fact, both cloud deployments and mobile applications have come to rely so heavily on APIs that you can’t have either without an API managing components somewhere along the line.
Many larger companies, especially those with a big online presence, have hundreds or even thousands of APIs embedded in their infrastructure. The growth of APIs will only continue to increase.
The ingenious thing about APIs is that many of them are just tiny snippets of code, and all are designed to be small and unobtrusive in terms of their network resource requirements. Yet they are also flexible and able to keep working and performing their main functions even if the program they are interfacing with or controlling changes, such as when patches are applied.
As amazing as APIs are, they also have their faults. Because they can be designed to do almost anything, from single functions repeated over and over to smartly controlling the advanced aspects of various programs or platforms, almost no standards govern their creation. Most APIs are unique, and many organisations simply create new APIs as needed. That can be a nightmare for security teams.
Another way APIs are attractive to attackers is that many are over-permissioned. Even APIs that perform only a few functions often have near administrator privileges. The thinking is that such a tiny API could not possibly do any harm.
Hackers compromise APIs and then use those credentials for new purposes, such as data exfiltration or deeper penetration into a network. According to security research conducted by Akamai, nearly 75 per cent of modern credential attacks targeted vulnerable APIs.
The problem is getting worse. According to Gartner, by 2022, vulnerabilities involving APIs will become the most frequently attacked vector across all cybersecurity categories.
API testing tools to the rescue
Having a critical networking and program component in the crosshairs of attackers is bad enough, but with APIs the situation is even more precarious because of the lack of standards involved in their creation. Many organisations likely don’t know how many APIs they are using, what tasks they are performing, or how high a permission level they hold. Then there is the question of whether those APIs contain any vulnerabilities.
Industry and private groups have come up with API testing tools and platforms to help answer those questions. Some testing tools are designed to perform a single function, like mapping why specific Docker APIs are improperly configured.
Others take a more holistic approach to an entire network, searching for APIs and then providing information about what they do and why they might be vulnerable or over-permissioned.
Several well-known commercial API testing platforms are available as well as a large pool of free or low-cost open-source tools. The commercial tools generally have more support options and may be able to be deployed remotely though the cloud or even as a service.
Some open-source tools may be just as good and have the backing of the community of users who created them. Which one you select depends on your needs, the security expertise of your IT teams, and budget.
Below are some of the top commercial API testing tools on the market and their main features, followed by some open-source tools.
Commercial API testing tools and platforms
APIsec
The APIsec platform acts like a penetration tool aimed at APIs. Whereas many tools can scan for common vulnerabilities to typical attacks like script injections, APIsec stress tests every aspect of targeted APIs to ensure that everything from the core network to the endpoints accessing it are protected from flaws in the API’s code.
One big advantage to APIsec is that it can be deployed in the development phase while APIs are being programmed. A full scan of apps that are in the process of being built takes only a couple minutes, with results comparable to old-school penetration testing operations that used to take days or weeks to complete.
AppKnox
AppKnox offers a lot of assistance to those who purchase and deploy their platform. Combined with its easy-to-use interface, this makes AppKnox a good choice for organisations that don’t have large security teams dedicated to their APIs. AppKnox starts with a scan to locate APIs either in the production environment, on endpoints or wherever they may be deployed. Once located, users can select which APIs they want to submit for further testing.
AppKnox tests for all the common problems that can cause an API to break or become compromised like command injection vulnerabilities in HTTP requests, cross-site tracing, and SQL injection vulnerabilities. This includes a complete analysis of web servers, databases and all components on the server that interact with the API.
After the API scan, users can submit their results for advanced analysis with a human security researcher, a process the company says normally takes between three and five days.
The Data Theorem API Secure platform is designed to fit into any continuous integration and continuous delivery/deployment (CI/CD) environment to provide ongoing security to APIs in every stage of development and into the production environment. Its analyser engine continually searches the network for new APIs and can quickly identify non-authorised ones or those that are part of the shadow IT at an organisation.
The analyser engine keeps itself up to date about the most recent vulnerabilities discovered for APIs and continually tests protected assets. It works with both on-premises and cloud environments to make sure that no APIs can fall victim to the latest threats.
To keep the CI/CD pipeline clear and flowing, Data Theorem API Secure offers to automatically fix discovered problems without requiring human innovation. That way organisations can keep their APIs secure against even the latest threats, so long as they are comfortable with a high level of automation.
Postman
While Postman certainly qualifies as a testing tool for APIs, its claim to fame is as a complete and collaborative platform for building secure APIs. It’s used by millions of developers working in Windows, Linux and iOS environments, and for good reason.
Postman provides developers with a complete set of API tools to use when designing new APIs, and it also provides a secure repository for code that organisations can build up over time. Using the secure repository can ensure that future APIs maintain tight security and organisational standards from the start.
The workspaces provided by Postman are designed to help developers organise their work. It also can provide security warnings when an app’s code starts to drift away from the organisation’s established secure template or incorporates a potential vulnerability. That way the problem can be fixed long before the API makes it to the production environment.
Smartbear ReadyAPI
In addition to security testing, the Smartbear ReadyAPI platform is designed to optimise their use and performance within any environment. It can execute an API security analysis with a single click, but it also supports other critical functions like seeing how well, or badly, an API can handle an unexpected load or sudden spike in usage.
You can configure ReadyAPI to generate the specific kinds of traffic that the API is expected to handle. It can also record live API traffic so that future tests will be more accurate and configured to the unique environment where it will be operating.
In addition, the platform can import almost any specification or schema to test APIs using the most popular protocols. Natively, ReadyAPI supports Git, Docker, Jenkins, Azure DevOps, TeamCity and more, and can be run in any environment from development to quality assurance long before APIs go live.
Synopsis API Scanner
One reason why the Synopsis API Scanner is so powerful is because in addition to security testing, it also incorporates fuzzing as part of its suite of deep scans and tests. The fuzzing engine sends thousands of unexpected, invalid or random inputs to APIs to see how they behave or if they will break when subjected to things like very large numbers or odd commands.
It also maps out all the paths and the logic of an entire API, including all the endpoints, parameters, authentications, and specifications that apply to its use. This gives developers a clear picture of what functions they intend their APIs to perform, compared with what they actually might sometimes do. It makes it clear why an API might be subject to unexpected behaviour or security vulnerabilities.
Open-source API testing tools
While the open-source tools generally don’t have the same support as commercial offerings, experienced developers can easily deploy them, often for free, to shore up or improve the security of their APIs. The following are some of the more popular offerings according to the open-source community.
Astra
Astra mostly concentrates on representational state transfer (REST) APIs, which can be extremely difficult because they are often constantly changing. Given that the REST architectural style emphasises scalability in its interactions between components, it can be challenging to keep REST APIs secure over time. Astra helps by offering to integrate into the CI/CD pipeline, checking to make sure that the most common vulnerabilities don’t creep back into a supposedly safe REST API.
crAPI
The crAPI tool has a terrible name, but it performs its function as an API wrapper efficiently. It’s one of the few wrappers that can connect to a target system and provide a base path with the root client’s default set of handlers. It can do it without having to create any new connections. Advanced API developers can save a lot of time with it.
Apache JMeter
Apache JMeter, which not surprisingly is written in Java, began life as a load tester for web applications but has recently expanded for use with almost any application, program or API. Its detailed suite can test performance on either static or dynamic resources. It can generate a heavy simulated load of realistic traffic so that developers can discover how their API will perform under pressure.
Taurus
Taurus provides an easy way to turn standalone API testing programs into a continuous testing operation. On the surface, Taurus is simple to use. You install it, create a configuration file and let your testing tools do their work. If you poke under the hood a bit, you can discover ways to generate interactive reports, create more complex scenarios to put your APIs through, and set up failure criteria so you can immediately go in and fix discovered problems.
This Article Source is From : https://www.channelasia.tech/article/691524/10-top-api-security-testing-tools/
#testing tools#security testing tools#API security testing tools#software testing#API#kairostech#kairos
0 notes
Text
Rdp Ms

Rdp Mac To Windows
Rdp Ms
Rdp Marathon Press
Rdp Madeira
The new microsoft edge browser reviews. Whether you use Microsoft Remote Desktop Services, Windows Virtual Desktop, Citrix XenApp, Citrix XenDesktop, or VMWare Horizon View to satisfy your organization’s Server Based Computing needs, we offer remote desktop management software for organizations of all types and budgets.
What is RdpGuard and How does it Work? RdpGuard is a host-based intrusion prevention system (HIPS) that protects your Windows Server from brute-force attacks on various protocols and services (RDP, FTP, IMAP, POP3, SMTP, MySQL, MS-SQL, IIS Web Login, ASP.NET Web Forms, MS Exchange, RD Web Access, VoIP/SIP, etc). Jan 11, 2018 Long story short - users are going to start using RDP on the conference room PC as opposed to signing into their own Windows account. A dedicated account will always be logged in with only the RDC icon on the desktop; basically everything else will be locked down through group policy. We would like to show you a description here but the site won’t allow us.
In addition, our solutions excel at monitoring RDP performance, connection quality and latency, security, and user session activity – we cover the gap in RDP monitoring and analytics for organizations that have deployed a pure Microsoft Remote Desktop Services environment with no Citrix or VMWare overlays.
> Not sure where to start? Answer a few brief online questions about your remote desktop protocol needs and get going now.
Deployment of our tools is a snap, regardless of your environment. Our solutions work well with on-premises networks or in datacenters serving up dedicated and shared desktops for Managed Service Providers. You can store collected terminal server data in SQL Server Express, on-premises SQL Server, or perhaps most conveniently, in Microsoft Azure SQL.
Finally, you will not find a more affordable set of solutions for Remote Desktop Services monitoring and management in the market. A subscription to our flagship RDS monitoring and reporting tool, the Remote Desktop Commander Suite, can be started for only $9.99 per server per month, with volume discounts available. Other software companies will charge you thousands of dollars to perform assessments of RDP and terminal server performance in your network – we do not.
Read on to learn more about the different editions of our products.
Remote Desktop Commander Suite
The Remote Desktop Commander Suite provides active, real-time and historical capabilities for user session management.
Historically, small and medium sized businesses have had few affordable options if they wish to monitor performance and user activity on their remote desktop servers. Vendors like Citrix and VMWare offer comprehensive remote desktop management software and terminal server monitoring solutions only at their top licensing tiers, placing them out of reach except for the largest organizations. Other third-party vendor solutions are often priced by concurrent user, making them expensive to implement and maintain.
The Remote Desktop Commander Suite is a powerful package for SBC environments. At its heart are two key components:
Rdp Mac To Windows
Remote Desktop Reporter
Remote Desktop Reporter, part of the Remote Desktop Commander Suite, is a comprehensive reporting and monitoring solution that collects and consolidates key metrics from all of the remote desktop servers in your environment, providing you with easy to run and schedule reports showing user activity, time tracking, licensing trends, application usage, and performance.
SPL Tracker (Service Provider Licensing Tracker)
SPL Tracker – part of the Remote Desktop Commander Suite – saves time, money, and headaches for organizations who need to keep an eye on service provider licensing programs.
Here’s how:
Microsoft SPLA Licensing, Citrix Service Provider Licensing, and the VMWare Service Provider Program offer big savings to Managed Service Providers, but at a price. Monthly reporting requirements are onerous, and MSPs that attempt to tackle this chore by hand find that it is time-consuming and error prone.
Wouldn’t you rather leverage a tool that can automate this task for you? And, while doing so, track and eliminate license wastage so you can reduce your monthly costs? If so, Service Provider Licensing Tracker is designed especially for you. Reach out and request a quote to learn more about how it can actually pay for itself in very little time.
Rdp Ms
Remote Desktop Commander Lite
If the Remote Desktop Commander Suite sounds too robust for your needs or you are still a fan of RDPSoft’s legacy Remote Desktop Admin Toolkit, then Remote Desktop Commander Lite is perfect for your needs.
Remote Desktop Commander Lite assists you with tasks that are active and real-time in nature, such as observing memory use by application or user, logging off and disconnecting users, terminating hung processes, and running parameterized PowerShell queries against session hosts, users, or processes.
Ipod touchcopy mac download. Best of all, Remote Desktop Commander Lite is now completely free – it’s our gift to entire RDS/Citrix community, and we hope it makes their lives easier.
Remote Desktop Commander Premium Management Features
If you don’t need all of the features of the Remote Desktop Commander Suite, but if you need improved shadowing and remote assistance capabilities to support your users, sophisticated real time monitoring of live sessions, and/or a way to delegate management tasks to your support staff without making them server admins, then extend the capabilities of Remote Desktop Commander Lite with our Premium Management Features package.
The Remote Desktop Commander Premium Management Features license only costs $99.99 per admin or help desk user per year, but gives you the power you need to adequately support a Microsoft Remote Desktop Services or Windows Virtual Desktop environment of any size. Microsoft Remote Desktop Services does not have a native mechanism to delegate remote desktop management tasks to support staff, which to date has required giving support staff admin rights. Also, native shadowing support for Windows Server 2012 R2, Server 2016, and Server 2019 has been complicated at best, plagued with issues related to shadowing multiple monitor sessions.
Our Premium Management Features package fixes both of those issues, by providing a complete RDS Management Delegation Wizard to define and extend granular rights to help desk staff across session hosts and connection brokers. It also comes with our new SuperShadow tool, which allows admins, support staff, and managers to monitor and assist multiple sessions at once, with file transfer capabilities through the clipboard, complete multi-monitor support, and so much more.
Remote Desktop Canary
Need to keep a constant watch on your Remote Desktop Services deployment, with the ability to receive instant alerts if new RDP connections cannot be established or if new connections are experiencing slow RDP login times? Want to review screenshots of login sequences to see how long it takes for RemoteApps and login scripts to launch? Want to send login statistics to your existing NMS solutions’ dashboards?
If so, Remote Desktop Canary is the RDS synthetic monitoring solution for you. Program it to perform recurring RDP login monitoring tests into your environment, notifying you and recording screenshots and other statistics for troubleshooting. Pricing starts at only $499.99 a year to monitor a single RDS farm/collection, with volume discounts available.
Other Services
Rdp Marathon Press
In addition to producing Remote Desktop Commander Suite and Remote Desktop Commander Lite, we also provide additional services for our clients.
You can request an RDS Performance Audit of your RDS infrastructure to review and identify any performance bottlenecks in the areas of CPU/memory consumption, network connection quality, and much more.

Rdp Madeira
You can also contract with us to produce custom reports against Remote Desktop Commander’s database.

0 notes
Text
Prepare for Microsoft 70-465 Certification with CertMagic Training:
A Microsoft 70-465 certification could be a strong factor in advancing in your current job or getting a new job elsewhere. But remember: to earn a Microsoft certification, preparing yourself for the exam will give you the greatest chance of success.
CertMagic is a Microsoft Gold Learning Partner, providing world-class training on a multitude of Microsoft products. All of our Microsoft courses are taught by Microsoft Certified Trainers and follow the official Microsoft curriculum. Learn more about our Microsoft technical training and certification courses here, and get started on advancing your career now.

Tips for Passing Microsoft Designing Database Solutions for Microsoft SQL Server 2012 Certification Exams:
Before taking a Microsoft Designing Database Solutions for Microsoft SQL Server 2012 certification exam, you need to be prepared to increase your chances of success. The following are practical tips and resources to help you study for your Microsoft certification exam.
1. Establish a Study Routine
Give yourself some structure when it comes to studying, and prioritize your study time. If you don’t, it’ll be way too easy to procrastinate or ignore what you need to do.
Figure out when you can absorb new material the best. When will you have the least number of distractions? If you have kids, for example, it might be the easiest to study after they’ve gone to bed or before they get up in the morning.
2. Review Topics Covered on the Exam
Microsoft 70-465 certification exam are very detailed — so much so that even deeply experienced professionals have failed. The questions are designed to challenge your knowledge, so it’s not advisable to just guess and hope for the best.
While you can’t know everything, you can get a head start with studying if you know the objectives and sub-objectives of each exam. Microsoft publishes the exam descriptions for all exams and lists their objectives. Each sub-objective will also have a set of skills that you’re going to be tested on, so review this page as much as possible until you’re comfortable.
3. Find Study Materials
Get study materials from legitimate sources that are authorized by Microsoft. Microsoft publishes its companion content online, and you can seek out online resources and forums from people who have previously taken the exam.
You can also take role-based certification training from a Microsoft Certified Trainer like New Horizons. Certified training companies have access to official Microsoft course-ware, which aligns directly with the objectives in the exams. Role-based certification training courses, such as our Azure training, SQL Server training and Dynamics 365 training, can all help you dive deeper into a specific role while preparing for your exam.
4. Take Notes While Studying
"If in doubt, write it out.” Write down every technical detail you see while studying for any Microsoft Certification exam. Since Microsoft’s exams are notoriously detailed, this could be a lifesaver. While what you write down might not be on the exam, it’s better to be safe than sorry.
Want to keep your notes organized for future reference? Consider using a note-taking app like Evernote or OneNote. Each has different features, so decide which one best suit your needs.
5. Practice Using the Technology
Hands-on experience will be invaluable as you take the exam. Instead of trying to answer questions about a theoretical practice you’ve only read about, you’ll have real-life knowledge of what a task does. But not everyone has access to technology like a sandbox data center to experiment with.
Taking a course from a Microsoft-certified training company should allow you to test your knowledge of the product in a lab environment. You can also sign up for a trial account to get familiar with most Microsoft products, including Azure, SQL Server, Windows and Dynamics 365.
6. Take Practice Exams
One of the most valuable things you can do to prepare for your final exam is take practice exams first. Treat the practice exams like real exams so that you understand what your approach should be when the big day comes. Expect to fail your first practice exam. Afterward, go through each wrong answer to determine your areas of weakness. Find out how to take an official practice exam here.
7. Relax on Exam Day
When it’s time for the exam, the best thing you can do is relax, knowing that you’ve prepared to the best of your ability. While you need to take every question seriously, going into the exam stressed and overwhelmed will increase your chance of failure. Perfection is not the goal; completion is. Let yourself off the hook by understanding that it’s okay to miss a question, occasionally guess or get confused by a question’s wording. You can always retake the exam if necessary.
Get the Guarantee Success with Real & Valid Study Dumps: https://www.certmagic.com/exam/70-465-exams
Good luck For Your Exam,
0 notes
Text
300+ TOP IBM TIVOLI Interview Questions and Answers
IBM Tivoli Interview Questions for freshers experienced :-
1. The Run as Administrator option is used to bypass user account control specifically on which operating system? Windows 2008 2. Which service access point is created on the target computer during the Tivoli Common Agent installation? Agent-Server (IPv4 / CommonAgent) 3. Which statement is true about static groups? Members can be added anytime after group creation. 4. Which supported database can be used by IBM Tivoli Provisioning Manager V7.2 on a Windows server? IBM DB2 5. What are the two main catalogs managed by the image library? 1. Saved Images 2. Master Images 6. What are your daily activities? TSM Server DB and Log size monitoring, client and admin schedule monitoring and library media management. I also have to install and configure TSM BA clients whenever required and troubleshoot backup/restore issues if any. 7. What are first * and second * in the “Query Event * *”? First * is Domain name, the second * is schedule name 8. How to check admin schedules status? Query Event * t=a 9. Where/How will you see, if errors occurred in the tapes? We can check it in actlog for hardware/media & read-write errors by using the command – “q actlog se=errors” To determine read/write errors for a particular volume run the command “q volume f=d“. This output will show the number of read/write errors occurred to that particular volume. 10. What is your DB size in your environment? Approximately 60 GB. Tip: size depends on your environment

IBM Tivoli Interview Questions 11. What is your tape model? HP LTO4 tape – capacity 800 GB, speed is 120 MB/Sec. 12. Have you done the DR test? Yes, In our environment we should do DR drills for every 6 months to ensure we are ready for any disaster recovery. 13. Have you done a library configuration? Yes, I did it once. 14. What is your library model? IBM 3584 library model with 4 drives 15. Can you explain how to install and configure the tdpsql? STEPS TO INSTALL AND CONFIG TDPSQL 16. What is the use of a maximum number of mount points parameter? Maximum parameter is used to increase/decrease the client backup/restore sessions. This parameter value should not be greater than available tape drives. 17. What are the TSM server tuning parameters? DBMEMPERCENT EXPINTERVAL MAX SESSIONS MOVEBATCHSIZE and MOVESIZETHRESH RESTOREINTERVAL TCPNODELAY TCPWINDOWSIZE TXNGROUPMAX 18. What is collocation? Where will you update it? Collocation is the process of keeping the client backed up data in a minimum number of tapes. Collocation can be done by nodes, node groups and by Filespace. We will update collocation while defining or updating storage pool definitions. update stgpool colloc=node 19. What is cloptset? Where will you update it? Cloptset is used to define a name for a set of options which you can assign to clients for archive, backup, restore, and retrieve operations. We should first define a clioptset name by using “define cloptset” command and then define each client options to that cloptset by using “define clientopt” command. Then you should use this cloptset name while defining any client node. Generally, cloptset is used to assign extra client options for any particular node from the TSM Server end without logging into the client machine. 20. Have you performed TSM DB restoration? Yes, 21. How will you see the errors in the tape? To determine read/write errors for a particular volume run “q volume f=d“. This output will show the number of read/write errors occurred to that particular volume. 22. What will you do if u find errors in the tapes? First, we have to figure it out the source of the error, whether tape drive has caused the error or tape itself has some problems. If the tape drive is the culprit make sure no other tapes are mounted on that particular tape. If tape itself has problems, then audit that tape by using “audit volume fix=no” command. This will show if there are any damaged files. IF there are no damaged files move the data from that tape to another tape, if there are any damaged files then we should restore the contents of that tape from the copy storage pool. 23. Have you done a manual backup? Yes, We can do it by the BA client command line and also through the BA client GUI. 24. How will you login into the client machine do you have any credentials for you separately? Yes, I have client login credentials with limited privileges. 25. How many servers in your environment? 3 TSM Servers 26. What is the TSM library manager? TSM LIBRARY MANAGER 27. On which TSM Server you will define tape drives in a shared tape library environment? We have to define all the drives on both the Library Manager and Library clients. CONFIGURATION OF TSM LIBRARY MANAGER 28. How will you see the lanfree backup process in the server side? By running “storageagentname:q session” Querying act log for “ANR0415I” message which says that “session 101 was proxies by storage agent S1 for node N1” You can also check the backup report for total lanfree bytes transferred. 29. How will you clean the drive? Generally, tape library will have separate cleaning drives, we have to just mount that drive through Library GUI. OR From TSM Server we can run “clean drive” command, this will also mount the cleaning cartridge/tape onto the drive and starts cleaning. 30. How to label the volume? If new tapes are kept in I/O exit port, run this below command label libvol search=bulk labelsource=barcode checkin=scratch TROUBLESHOOTING TAPE LIBRARY 31. What are the parameters in the copy group? a version exists, version deleted, retention extra, retention only, serialization, destination, mode, frequency …… etc. 31. What is the use of reclamation? Reclamation makes the fragmented space on volumes usable again by moving any remaining files from one volume to another volume. This action makes the original volume available for reuse. 32. Is there any chance of moving inactive data from one volume to another using reclamation? No, reclamation will move both active and inactive data. 33. What is audit volume? Audit volume command is used to check the inconsistencies between database information and a storage pool volume. 34. What is fix=yes/no in audit volume command? Fix — Specifies how the server resolves inconsistencies between the database inventory and the specified storage pool volume. Fix=No — Tivoli Storage Manager reports, but does not delete, database records. Fix=Yes — The server fixes any inconsistencies as they are detected 35. What is migration? use of migration? Migration is used to move client files from one storage pool to the next storage pool in the storage hierarchy. The migration will make some empty space in disk pools which can be used for taking a backup of the client machine. 36. Have you done up gradation? which method you have used? Yes, we used the Same System Media Method 37. Have you done upgradation for client machine? Yes, First we have to copy all the important client configuration files, disconnect the connection with TSM Server and then uninstall/install new client version. 38. Have you done the installation of TSM server? tell me the procedure? TSM SERVER 6.3 INSTALLATION STEPS 39. Explain the log flow in the 6.3? RECOVERY LOG IN TSM VERSION 6.30 40. What are the details available in the dsmsched.log and dsmerror.log? dsmsched.log & dsmerror.log will contain the client schedule status details and any schedule error details. 41. Will the lanfree data go to the disk pool? No, Lanfree data will go directly to tape/tape pools. If we have a disk library in a SAN, then we can send lanfree to disks but we need another supporting software. 42. How to see the DB size? Query db f=d 43. How to check the paths? query path f=d 44. How to update path? update path source name destination name srctype=server desttype=drive/library device=devicename online=yes 45. What is the difference between search=yes and search=bulk in LABEL command? YES – Specifies that the server labels only volumes that are stored in the library BULK – Specifies that the server searches the library entry/exit ports for usable volumes to label 46. In tdpsql what does tdpsql.cfg file contains? It contains all the tdpsql performance monitoring parameters like Buffers, Buffers size, SQL buffers, SQL buffer size, data stripes, and log file, etc. 47. How to install tdpsql in the client machine? INSTALL AND CONFIGURATION OF IBM TDPSQL 48. Any idea on TSM Offsite Reclamation? OFFSITE RECLAMATION PROCESS 49. What is the use of storage pool backup (copy stgpools)? If there are any read/write errors on the primary pool volumes, we can restore them from copy pool volumes. 50. How to do Lanfree configuration? STEPS TO INSTALL AND CONFIGURE TSM STORAGE AGENT 51. Explain about policy management? TSM POLICY MANAGEMENT BASICS & POLICY STRUCTURE 52. What are the parameters in the copy group? a version exists, version deleted, retention extra, retention only, serialization, destination, mode, frequency …… etc 53. What is Serialization? It specifies how Tivoli Storage Manager processes files or directories when they are modified during backup processing. IBM Tivoli Questions and Answers Pdf Download Read the full article
0 notes
Text
Take the Flight of Success with the Stunning Tableau Training Courses
Get experience in the Tableau training with the best professionals. The certified training package is genuine. The excellent trainer in the institutes will provide the best course service to the students. This is the best training for beginners. This course gives the 100% job placement to the students. The Tableau is a course contains an overview of Tableau, data visualization, connecting Excel data.
Explore Various Data Representation Skills
The Tableau Training in Bangalore with top faculty will provide you the exclusive course in the institute. You can get online course with flexible timings. Tableau server manages security and the sharing reports. The well designed classroom and lab facility is the best service given by the institute. You can watch online demo and avail free training classes. The certificate oriented courses give you the excellent training courses with well experienced experts. The Tableau syllabus is included marks, highlighting, working with dates, etc. The practical and theoretical classes will offer the best course in the industry.
Experience Real Time Training Program
The online course of Tableau will reinforce you to exposure of real world requirements. Tableau connects to a lot of other databases. This has the 24 online courses you can avail anytime. You will get lifetime support and the course will ensure to help you with any technological assignment projects. The institute provides you the resume preparation and also makes you prepare for the mock interviews. The free demo classes will make you understand about the course and you can choose the course after attending the free trial class. The institute offers Selenium training classes for the working professionals.
Learn Core Java through Selenium Training
Learn the basic of the Tableau course from the best institutes in Bangalore. You can learn page object framework using the testing selenium web driver. Experience how doing automate Ajax based application using selenium. The institute provides interview questions for Tableau training. Become the Tableau expert by enrolling in the training course. The course offers practical guidance and also the course is available in multiple training locations. The training is provided in the well-equipped lab and classroom.
Extraordinary Knowledge Transfer with the Training
The Tableau training will give you a real time career course. The excellent trainer will offer you the exclusive courses to the students for a better career. The well-organized training course will give you a unique knowledge of software application and course materials. The course offers good structured modules and the experts strive to clear the doubts of the students. The good real time examples would explain in the class during the training process. The real time course will offer in the institutes with reasonable fee. The world class equipment provided by the institutes for the beginners and advanced level students. The fast track training on Tableau major topics cover with formatting, building interactive dashboard. The certified courses will give you the certification oriented training for a better career. Subscribe in the best institutes for a certified course with reasonable fee structure.
DataBytes; leading Software Training Institutes in Bangalore offers Software Testing Courses (QTP, Selenium), Tableau / Qlikeview, Java, Adv Java, Dot NET, SQL /PL SQL, Python, ETL, Hadoop, BIG Data, Android, , Informatica, AutoCAD etc.
#software testing training#Software Testing Training Institutes#software training institutes in bangalore#Software Testing Training Institutes in Bangalore#software testing training in bangalore#python training in bangalore#python training#python training institutes in bangalore#python training bangalore#python course#tableau training#tableau training in bangalore#tableau course#tableau training Institutes in bangalore
1 note
·
View note
Text
“Mastering Full Stack Development: Essential Topics for Success”
Absolutely! I’m eager to explore the world of full-stack development alongside you. My expertise in this domain has grown significantly, and Selenium has gained widespread recognition, being extensively employed across diverse industries.

To Become A Full Stack Developer, One Needs A Diverse Skill Set, Including Proficiency In:
1. Front-end Development:
HTML
CSS
JavaScript
Front-end frameworks like React, Angular, Vue
2. Back-end Development:
Server-side languages such as Node.js, Python, Ruby, Java
Databases like MySQL, PostgreSQL, MongoDB
Server-side frameworks including Express, Django, Ruby on Rails
3. Database Management:
Database design and modeling
SQL (Structured Query Language)
4. Version Control:
Git and GitHub
5. APIs (Application Programming Interfaces):
Understanding of RESTful APIs and GraphQL
6. Web Servers and Deployment:
Familiarity with web servers like Nginx, Apache
Knowledge of deployment strategies such as Heroku, AWS, Docker
7. Command Line/Unix:
Proficiency in basic command line navigation and operations
8. Development Tools:
Utilization of text editors or Integrated Development Environments (IDEs)
9. Basic Design and User Experience (UX):
Implementation of responsive design
Adherence to usability principles
10. Testing:
Application of unit testing and integration testing
11. Security:
Adherence to web security best practices
12. Agile and DevOps:
Understanding of Agile methodologies and DevOps practices
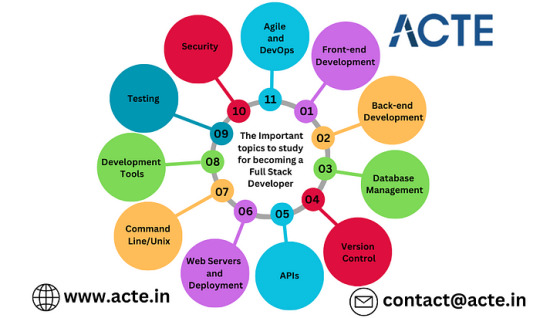
In the dynamic field of web development, continuous learning is crucial. Stay updated on new technologies and industry trends.
If you’re keen on exploring Full-stack Developer course in Chennai, I highly recommend considering Top Institutions. They provide certification programs and job placement opportunities, guided by experienced instructors to enhance your learning journey. These resources are available both online and in-person. Enrolling in a course step by step could prove to be a valuable decision if it aligns with your interests.
I trust this addresses your query adequately. If you have more questions or need further clarification, please feel free to ask in the comments section.
If you’ve found this information valuable, I invite you to follow me on this platform and give it an upvote to encourage more discussions and insights about Full-stack Development. Your time and engagement are greatly appreciated, and I wish you a wonderful day ahead.
0 notes
Link
Now, Microsoft is truly one of the most instrumental solutions in shaping your IT career. It has been in the industry for ages! With its long-running history, you definitely won’t go wrong with their line of qualifying badges.
As a top-rated IT organization, their certification program is continuously modified to ensure relevance among IT professionals. And with their current revision, it resulted in some drastic changes to their certification track. These include the retirement of a part of credentials from their previous technology-based program.
Evolution of Microsoft Certification Track
For many years, Microsoft has been focusing on technologies mostly, which has resulted in the appearance of its AZ-300 dumps, and MCSD levels of certifications. These are sought-after credentials still immensely utilized by thousands of IT practitioners. But even with the popularity of this program, a number of its badges has been retired due to the constantly changing IT environment.
And of course, Microsoft strives to make certain that they only offer the best and the most up-to-date services and products to businesses, individuals, and organizations. As a result, they have created a new program that targets mostly role-based skills and knowledge in its updated credentials. The respective levels are as follows: Fundamentals, Associate, and Expert.
Collection of MCSA Certification Program
Despite the retirement of most previous certifications, there is still a handful of Microsoft badges at, say, MCSA level which are still considered relevant. And if you’re unsure what certification to pursue, here are the top five of its most in-demand associate-level badges that are available up to present.
MCSA: SQL Server 2012/2014
Eyeing to become competent in terms of SQL Server 2012/2014 databases? Well, you’ve got to pursue this MCSA certification. To earn it, you’ll need to complete three tests, which are 70-461, 70-462, and 70-463. For your information, exam 70-461 highlights SQL Server 2012/2014 querying, 70-462 test deals with Microsoft SQL Server 2012/2014 databases, to be more precise, their managing, and exam 70-463 supports your knowledge of using data warehouse with SQL Server 2012/2014.
These certification exams are designed for those with a background in database administration and development, along with system engineering.
MCSA: Windows Server 2012
Next on the list is MCSA: Windows Server 2012, a certification that proves your professional prowess as a network administrator or a computer network practitioner. You will need to complete 3 equally challenging exams before you earn this credential. These are 70-410 exam in Windows Server 2012 Installation and Configuration, 70-411 exam in managing Windows Server 2012, and 70-412 exam in working with the Advanced Windows Server Configuration. At the same time, if you prefer a direct, all-in-one exam, you can opt for 70-417 test instead, being is a mixture of all the three above tests qualifying you for Windows Server 2012.
And if you want to further advance your Windows Server 2012 abilities, you can continue your learning up to earning the MCSE: Core Infrastructure credential.
MCSA: Web Applications
Another outstanding badge is MCSA: Web Applications that exhibits your breakthrough expertise in creating and managing modern web applications. But before you become an expert in programming business logic for diverse application types, you need to undergo its required associate-grade exams. Here, candidates are given two prolific options: taking exam 70-480, together with 70-486, or attempting 70-483 plus 70-486 test.
To give you an overview, exam 70-480 discourses about HTML5 programming via CSS3 and Java Scrip, while exam 70-483 mainly deliberates on C# programming. To wrap up your skills in web applications, you need to clear exam 70-486, which will deal with your proficiency in mastering ASP.NET MVC web applications. The best candidates for MCSA: Web Applications are individuals with a working knowledge of programming aiming to become a web developer or a web administrator.
MCSA: Microsoft Dynamics 365 for Operations
Also, part of the discussed top 5 is Microsoft Dynamics 365 for Operations, which is the endorsement of your mastery in working with various Dynamics 365 technologies and solutions. With this certification, you’ll become more adept with the basic and advanced operational tasks such as implementation, improvement, and customization of solutions.
To secure this credential, you have to accomplish two exams, 70-764 or 70-765, plus MB6-894. The perfect candidates for these exams in Microsoft Dynamics 365are professionals like programmers, IT personnel, and technical consultants. And before you make your decision to ace them, you should discover that MCSA: Microsoft Dynamics 365 for Operations is set to be withdrawn by June 30, 2020, so hurry up to acquire the credential.
MCSA: SQL 2016 Database Development
Database development in 2016 is a coveted MCSA certification because it seemly covers all the germane topics needed for a database professional. And, you will not just be restricted to local databases but also will master cloud-based features. So, if you want to transform into a database specialist, try your best to complete both 70-761 and 70-762 exams.
The first one assesses your capability in querying data via Transact SQL. The second exam, on the other hand, measures applicants’ mastery in developing and implementing SQL database solutions. And for you to have an effective certification journey, make sure that you already possess prowess in groundwork database functions, including writing queries. Some of the perfect professionals for this certification are database administrators, developers, and system engineers.
Best Dumps for Microsoft MCSA Exams
As you commence your test preparation, make a move to gather all important materials, both on-paper and online. So, start first with the Microsoft-endorsed references such as prep videos, self-paced and instructor-led training courses, and enrich them with valid vendor-elaborated practice tests.
Once you’ve completed learning with official resources provided by Microsoft, you can explore other notable websites. One of the most recommended supplemental web-spots for experiencing diverse MCSA exams is ExamSnap.com. Hence, all the exam dumps offered by ExamSnap are regularly updated to keep up with the changes in IT technologies and market demands. You are well-advised to taste their all-inclusive Premium Bundles equipping you with specialist-designed questions and answers for the tests, and more materials. Further, they both free and premium exam dumps smoothly work using the great VCE Player to give you an enjoyable and functional exam experience! If you are in doubts whether this website is worth your attention, try out their excellent collection of free exam dumps and make up your mind.
Bottom Line
Taking MCSA exams not just expounds your knowledge but also qualifies you as a specialist for a specific job position. This means that completing these certification exams highly defines your professional attitude. So, before the MCSA certification program gets phased out, explore its broad collection of badges, choose your specialty track, and expand your proficiency with actual and updated exam dumps!
The post Securing Various Microsoft MCSA Exams using Best Exam Dumps appeared first on Florida Independent.
0 notes
Text
Become a Microsoft 70-461- Querying Microsoft SQL Server 2012 Certified:
In today’s competitive world, technical certifications play an important role in advancing your Professional career. It is a great way to validate and sharpen your technical skills, thus helping you in being more productive in your assignments. It also helps you to stand out from the crowd and get more visibility. A few months back I decided to appear the Microsoft Exam 70-461: Querying SQL Server 2012/2014 and was able to successfully pass the exam. I have been working with SQL Server for more than 10 years, but I must admit that preparing for this exam was a great experience and I got to learn so many new things which I did not get a chance to work on during my day-to-day work. Everyday someone in the community plans to take this certification exam and I have bounced into multiple questions in social forums and groups asking for tips and guidance to pass the 70-461 Exam. This prompted me to come up with this article and share my experience with the community and hopefully it will be helpful for anyone who is planning to take this certification.

Skills Required
The 70-461 exam include questions from the below area:
Create database objects (20–25%)
Work with data (25–30%)
Modify data (20–25%)
Troubleshoot and optimize (25–30%)
And after appearing the exam I must admit that the questions were well spread across, as mentioned in the percentages above. No surprises there! My first suggestion will be to take this exam as an opportunity to learn more about SQL Server. No matter if you are a beginner or experienced SQL developer, there will be areas in which you do not have practical working experience – and those will be the areas where you need to first focus on. After going through the exam syllabus, I figured out that I need to practice more on few selected areas on which I do not get the opportunity to work often like XML Data type, Windowing functions, Transactions and Isolation Levels. Looking back, I think this decision paid off and I was able to successfully able to handle questions on these areas – though I was a bit surprised to find lot more questions from these areas than I had expected. You need to practice from Dumps or any online questions to pass the exam. one more thing you need to make sure that you practice writing SQL queries. Having just a theoretical knowledge won’t help you pass this exam. I would highly encourage you to download pdf dumps & software practice test of SQL Certification if you already don’t have it. You can then download a sample database and practice writing queries. There are lot of resources provided by CertMagic which will help you to answer some of the frequently asked questions about the certification exam.
You can get the Study Material @https://www.certmagic.com/exam/70-461-exams
Good luck,
0 notes